By Janio André Gutierrez, Product Manager, Incident Response and Recovery, and Benoit Gagnon, Vice President, Cyber Investigations and Incident Response
What do we know about the group?
The Lapsus$ group has built its credibility through the havoc it has wreaked on various companies since the early 2022s. While it is difficult to understand exactly what is going on in the minds of the group’s members, it is interesting to note that the group seems to stand out from what is generally seen in the hacking scene for essentially two reasons. First, the group does not appear to operate in a tightly knit fashion. The information available on the group tends to show that it operates more loosely than we are used to seeing in computer crime groups. This suggests that the members are dispersed across different geographic regions and do not operate under the aegis of a state.
Second, the motivations of Lapsus$ are not extremely clear. Although they recently stated in their Telegram group that their only goal was to make money, and that they were not politically motivated, the reality is less clear about their actual intentions. Lapsus$ is particularly vocal about its actions, which might suggest that the group’s reputation aspect also weighs in the balance – a behaviour not unlike what has been possible to see in Lulzsec, for example. Thus, the editorial line of the group does not seem to be completely defined yet and it will be interesting to see how it will take shape in the coming months.
Recent police arrests have taken place in the UK and seem to be directly related to the group. Information available as of March 27, 2002 suggests that the group is primarily a group of teenagers between the ages of 16 and 21 living in the London area. The main suspect in the case cannot be identified because he is a minor, but he is believed to be in possession of approximately 300 Bitcoins, the equivalent of about $14 million US at the time of the arrest (TIDY, 2022). While the group’s Telegram channel, followed by more than 53,000 people, was quite vocal until recently, it has been mostly silent since March 25. It remains to be seen whether the recent arrests will be enough to put the group down once and for all.
The feats of Lapsus$
Attacking Samsung
Just days after leaking data it claims to have exfiltrated from chipmaker NVIDIA, ransomware group Lapsus$ counts another global company among its victims. This time, it is releasing data allegedly stolen from Samsung Electronics.
The consumer electronics giant confirmed in a statement to the media that a “security breach” related to internal company data had occurred, but said customer and employee data had not been affected.
Lapsus$ had announced earlier on his Telegram channel that he had broken into Samsung’s premises and offered a taste of what he had as evidence, including biometric authentication information and source code from Samsung and one of its suppliers, Qualcomm. This is according to Security Affairs, which also published a screenshot of the data leak :
Nvidia attack
In February 2022, Nvidia, a company known primarily for its video cards, was hacked by Lapsus$; the group reportedly got its hands on about 1 Terabyte of data on Nvidia’s servers. In the aftermath, Nvidia confirmed that the group had gained access to privileged information belonging to the company, but also to some access belonging to employees.
An interesting element of the hack is that the group did not make an explicit financial demand. Instead, it demanded that Nvidia remove limits on the RTX 3000 series of graphics cards related to cryptocurrency mining by March 4. Otherwise, the group would leak secrets belonging to the company. Lapsus$ eventually put its plan into action by leaking various information about Nvidia employees. Laspsus$ also released an Nvidia certificate signing tool, now allowing cybercriminals to use it to issue certificates on behalf of Nvidia for malware.
Ubisoft attack
In early March 2022, Ubisoft suffered a cybersecurity incident that temporarily disrupted some games, systems and services, the company said in a press release. Ubisoft did not indicate who might be responsible, but the next evening, the Lapsus$ group took credit.
Ubisoft believes that at this time there is no evidence that any player’s personal information was accessed or exposed as a result of the incident and says that games and services are “now operating normally.” As a precaution, the company also has “initiated a company-wide password reset.”
Leak at Microsoft
Lapsus$ also gained notoriety for a high-profile attack at Microsoft. According to the Redmond-based company, the breach did not impact its customers’ data, however, it allowed access to several confidential information of the group, including the source code of several products.
The most ironic part of the story is that Lapsus$’s desire to make itself known has had the effect of reducing the impact of the breach. Indeed, Microsoft was not aware of the situation until Lapsus$ announced it publicly. Had this announcement not been made, Lapsus$ could have possibly done even more damage to the organization.
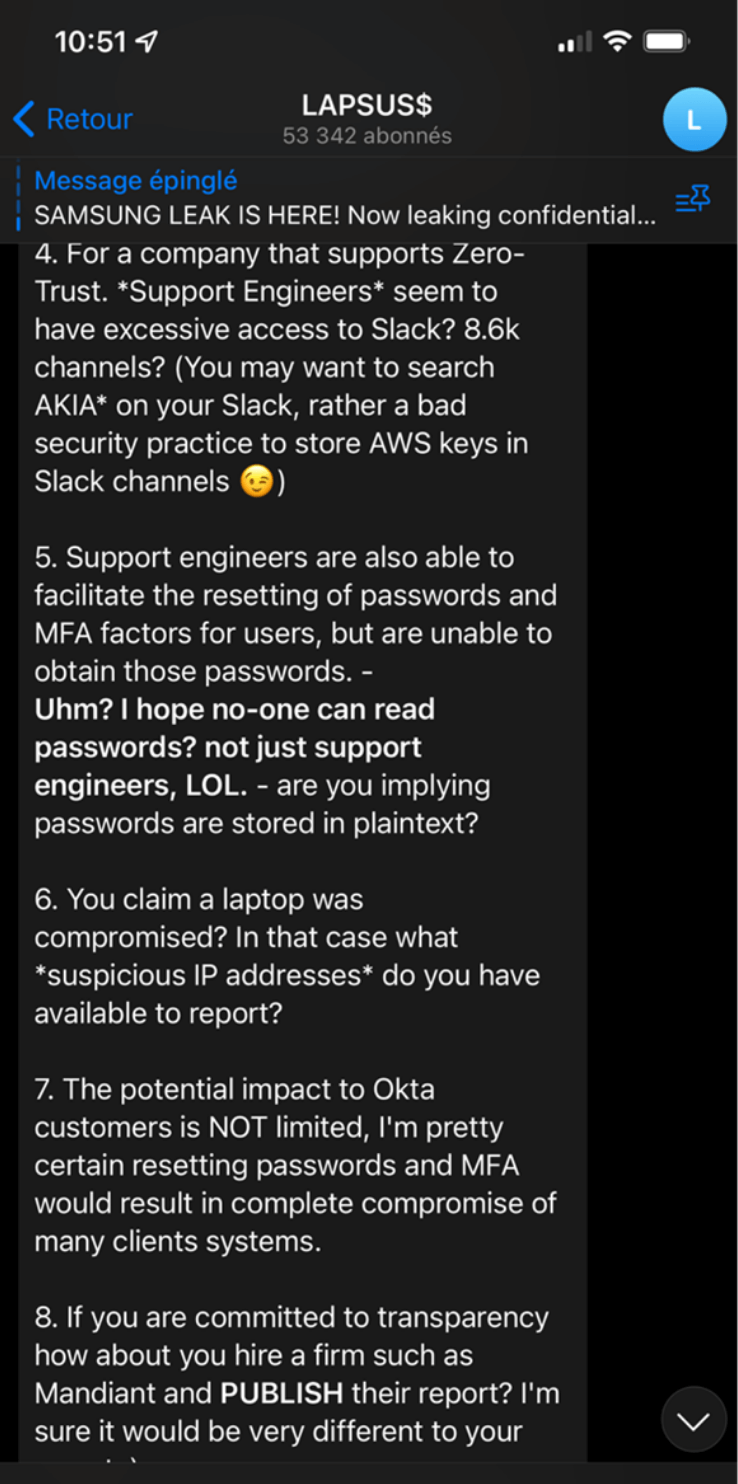
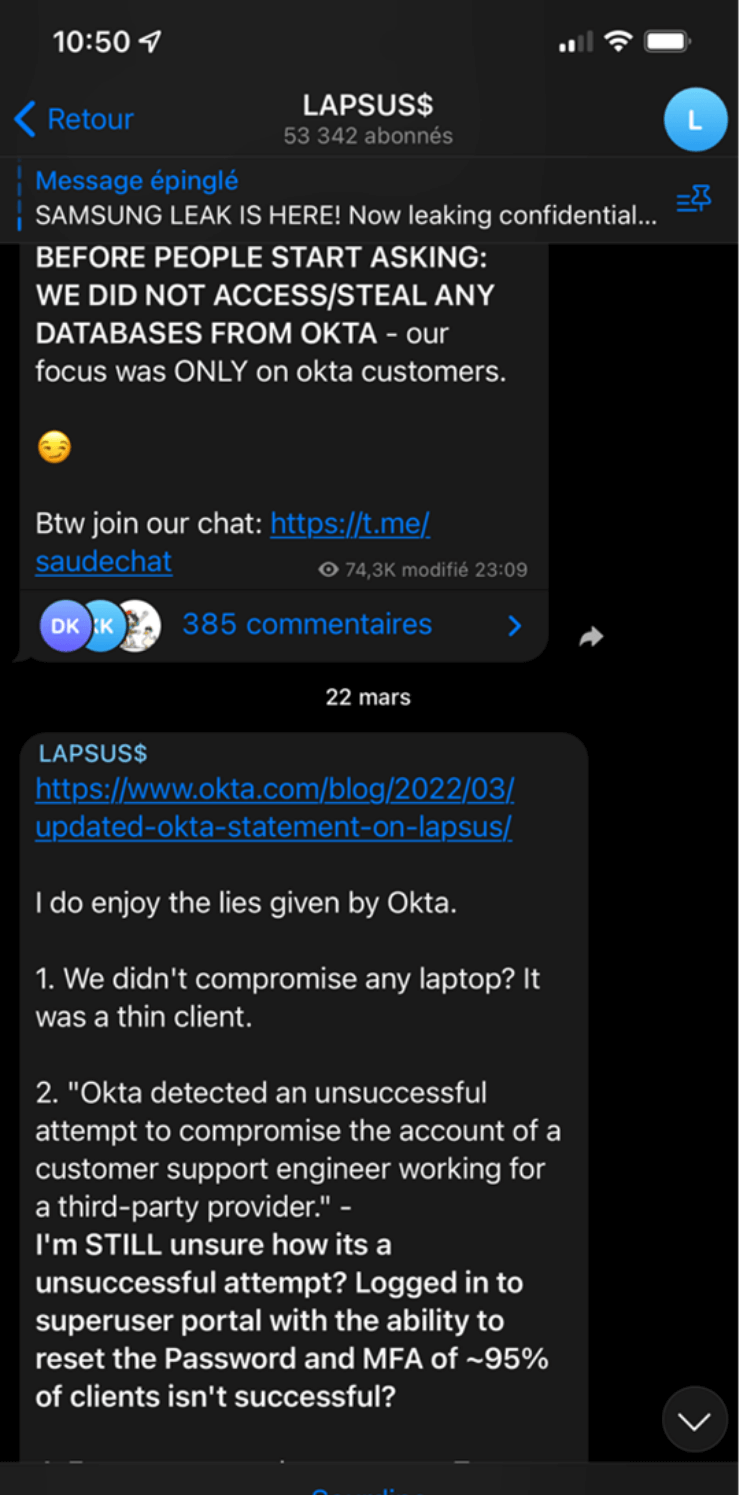
Okta’s breach
The latest big player to be pushed around by the activities of the Lapsus$ group is Okta, a U.S. company that works in the field of authentication software (NEWMAN, 2022). Okta explained how Lapsus$ managed to bypass security: the criminal group managed to compromise the remote access and account of an employee working for a subcontractor in charge of customer support. This would have allowed the group to access hundreds of customer records. Lapsus$ would have had the account in their hands over a period of about five days starting on January 16, 2022 – the whole thing was revealed by the group on March 17, 2022, however. Now, what seems to hurt Okta the most in this story is that the company detected the whole thing on January 20 and reported nothing. By revealing the whole thing, Lapsus$ has therefore tainted Okta’s reputation for not taking responsibility for a computer incident. The story does not say, however, whether any financial claims were made. Since then, Okta has investigated the matter and has been obliged to make a public mea culpa (BRADBURY, 2022).
An original modus operandi
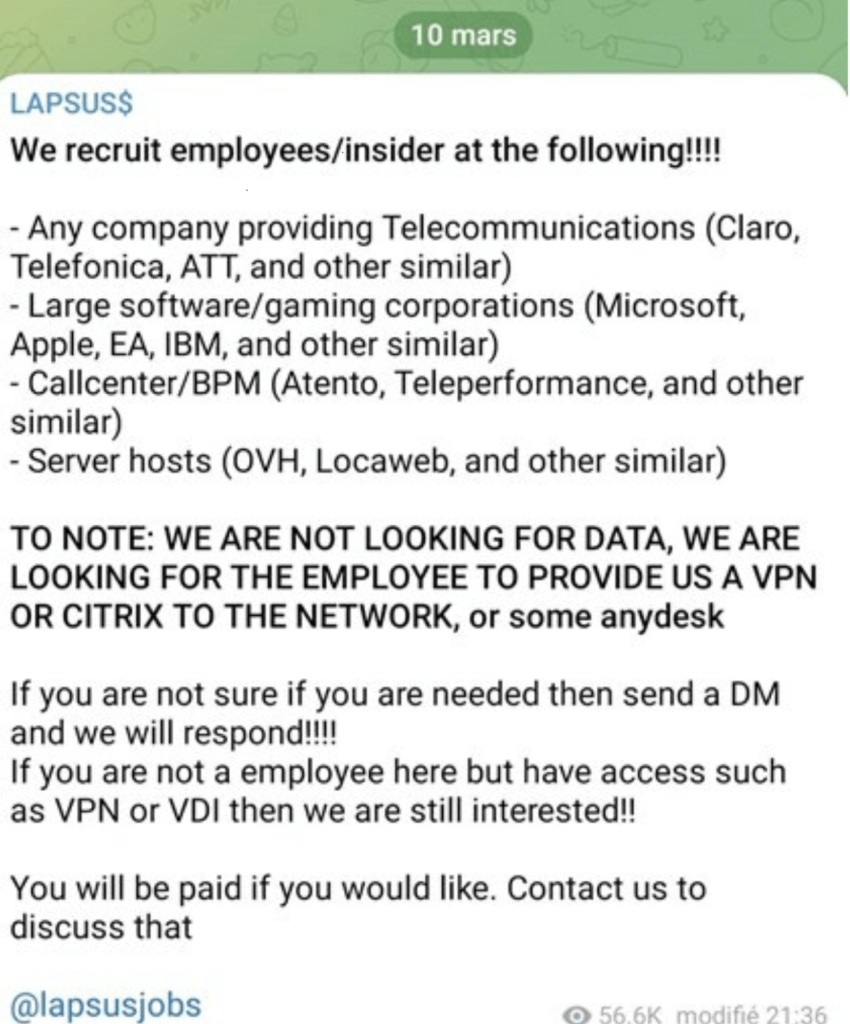
One of the important elements of the Lapsus$ group is its modus operandi. Indeed, its attack methodologies are somewhat different from what we usually see in the hacking scene. The group seems to be changing its way of doing things, abandoning the more traditional ransomware, in order to turn to ways of doing things that are related to somewhat different methodologies. In particular, it is interesting to see that the group is increasingly using data theft as a mode of operation. The group steals data from a target, and then pressures the target to pay an amount in cryptocurrency. In other words, this is more of an extortion on the reputation of the company than an attack via a data encryption tool classically seen in ransomware.
The techniques by which Lapsus$ achieves its goals also tend to be off the beaten path. The group is known to use SIM-swapping techniques, social engineering, and even attempts to bribe employees of companies targeted by the group, or their partners, in order to obtain privileged access or confidential data. This last method is in real contrast with some more classical techniques and risks to intensify the risk that an employee could concede to leak privileged information to third parties.
Only time will tell if Lapsus$ has been a shooting star in the world of cybercriminal groups. However, one thing is certain: it may have imprinted their modus operandi on the imagination of some other groups. Thus, his criminal innovation could well have the effect of influencing other players in the coming months, if not years.
Sources
BRADBURY, D. (2022, March 22). Okta. Retrieved from Updated Okta Statement on LAPSUS$: https://www.okta.com/blog/2022/03/updated-okta-statement-on-lapsus/
NEWMAN, L. H. (2022, March 28). Wired. Retrieved from Leaked Details of the Lapsus$ Hack Make Okta’s Slow Response Look More Bizarre: https://www.wired.com/story/lapsus-okta-hack-sitel-leak/
TIDY, J. (2022, March 24). Lapsus$: Oxford teen accused of being multi-millionaire cyber-criminal. Retrieved from BBC News: https://www.bbc.com/news/technology-60864283